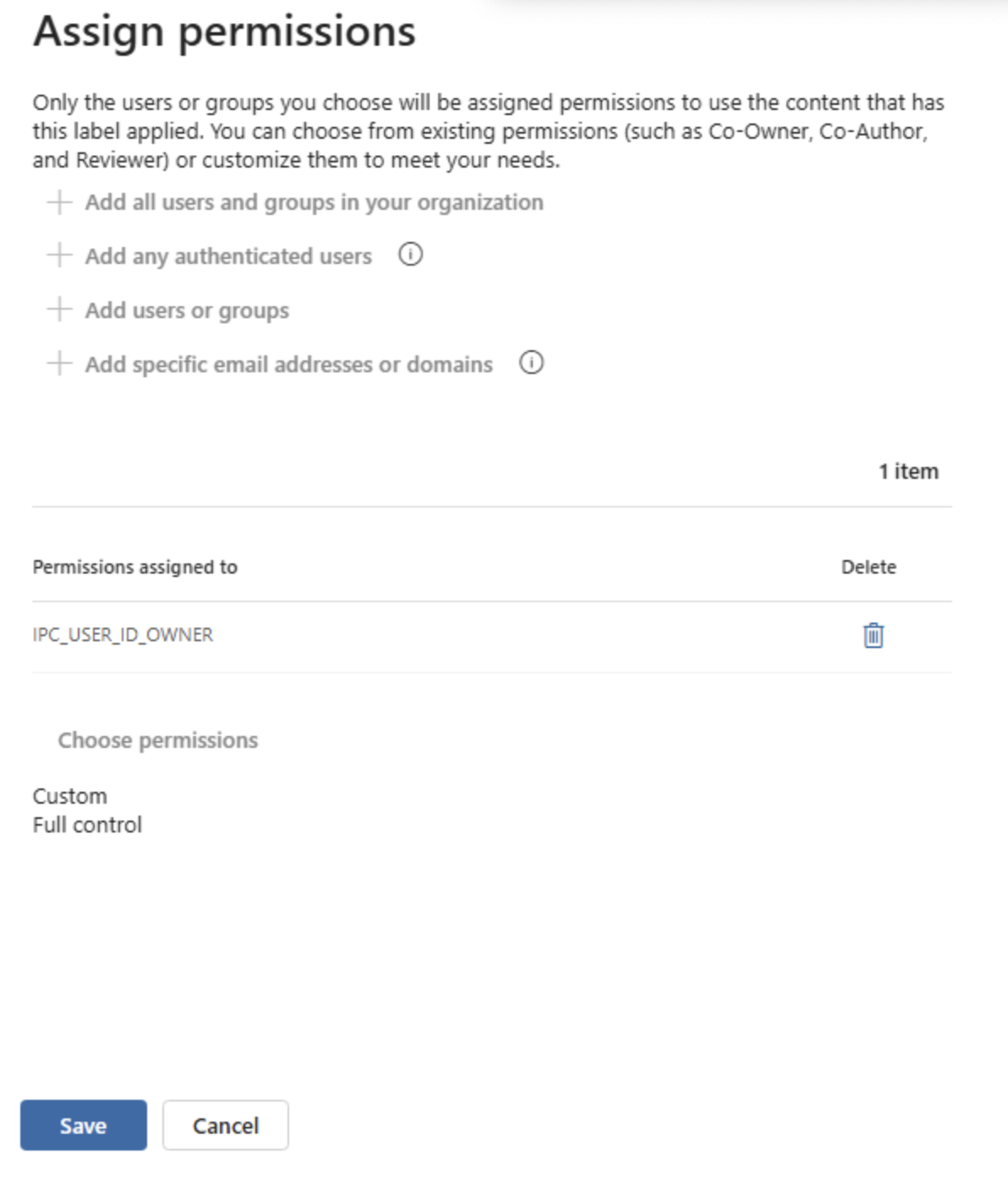
The structure described in this guide is used when there is a security requirement to restrict document access to all users except the document owner. There are two methods for creating sensitivity labels based on this encryption configuration: one is somewhat complex, while the other is very straightforward. This guide walks through both approaches.Related ConceptsIPC_USER_ID_OWNER:A reserved u..